

CyberSense shows you what is clean and what is compromised, so you can confidently identify your last known clean backup or snapshot, avoid reinfection, and restore operations quickly.
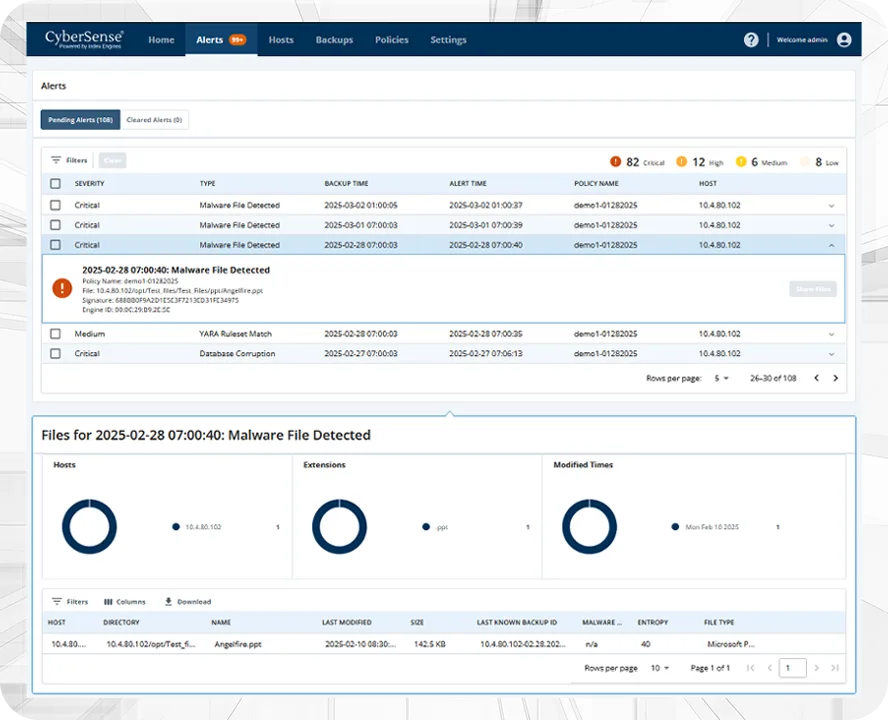
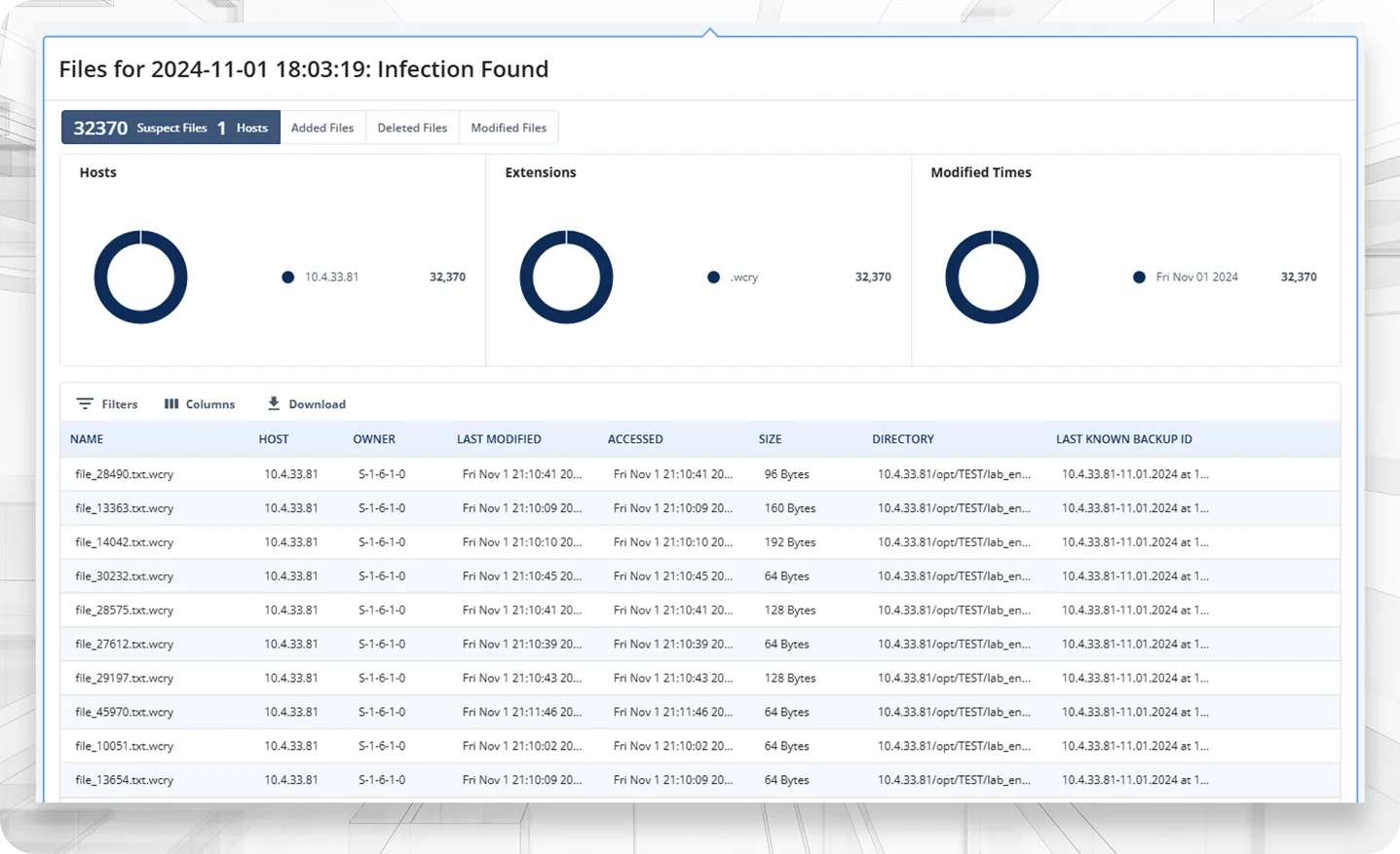

Ransomware Variants Analyzed
Customer Datasets Collected
Validated Accuracy

 ↑
↑